Cyber Security for SMBs: How Much is Enough?
11 June 2025By Jenna Polson | Cyber Security | No Comments
Should my business align with a cyber security framework?
Will that extra investment give me the right protection?
How do I know if my protections are still fit for today’s risks?
There’s no single, mandatory cyber security standard in Australia for non-government organisations. Instead, cyber security is generally about demonstrating that you’ve taken ‘reasonable steps’ to manage risks, particularly around data privacy, record-keeping and industry-specific regulations.
That’s where frameworks can help. They give you and your IT partner a structured way to assess risks, prioritise protections, and level-up your security posture.
Frameworks can also add credibility in the eyes of clients, partners and cyber insurers.
Is the Essential Eight really essential?
The Essential Eight Maturity Model, developed by the Australian Signals Directorate, is often seen as the go-to framework in Australia. It’s mandatory for government agencies and widely referenced in cyber security discussions.
On the surface, it’s appealing: a government-recognised checklist of eight practical measures, organised into three maturity levels.
But here’s the catch: the Essential Eight was designed for government contexts. It assumes:
- Large-scale, enterprise networks
- Microsoft-centric environments
- Budgets and risk appetites that reflect national-level assets and exposure
It’s highly prescriptive, focusing on specific measures in that context. That means, while it provides great detail on configuring Microsoft security settings, it says little about protections for non-Microsoft platforms. If you’re using Gmail, MacOS, or SaaS products like Xero or MYOB, these may remain vulnerable. The measures are also often overkill for SMB risk profiles and budgets.
The bottom line? The Essential Eight is not a good fit for many non-government SMBs.
In practice, insurers and partners care more about evidence of sound risk management, not strict framework compliance.
The real-world trade-offs
Let’s call it out: there’s no such thing as 100% protection. Even if there was, the benefits probably wouldn’t outweigh the costs, especially for SMBs.
Every cyber security decision involves a trade-off. Each potential security measure can only achieve two of three factors:
- Level of protection
- Budget
- Usability
The ideal balance is different for every business, and changes over time as your systems and risks evolve.
For example, multi-factor authentication is considered one of the cheapest and most effective ways to protect access to your business assets. However, it does introduce an additional step in the sign-in process, reducing usability a little.
Other options may improve usability, but at a higher cost.
Ultimately, the proportional approach focuses on outcomes, not box-ticking.
Outcome-focused, flexible frameworks
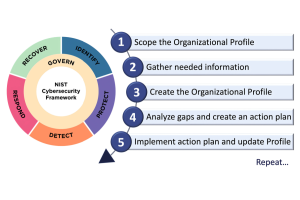
If you want the guidance of a proven framework, but with more flexibility, the NIST Cyber Security Framework (NIST CSF) is an excellent option.
Originally developed in the US and updated in 2024 (version 2.0), NIST CSF provides guidance to business leaders that is accessible, flexible and outcome-focused.
It’s organised around five core functions:
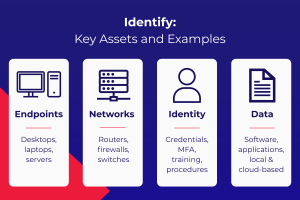
- Identify – Understand your assets, risks and vulnerabilities
- Protect – Put controls in place to mitigate risks
- Detect – Monitor for suspicious activity or breaches
- Respond – Have a clear plan for responding to incidents
- Recover – Restore normal operations and improve resilience
In our experience, many businesses underinvest in the first step: Identify. You can’t protect what you can’t see. That’s why we help clients map their assets, systems and risks: to build a complete picture of their security posture and opportunities to level up.
Expertise is essential
At Bigfish, we believe the right cyber security approach is one that fits your business, your risk profile, and your budget.
Your protections should:
- Be proportionate to your risk
- Evolve with the threat landscape
- Support your business goals
Whether or not you choose to align with a specific framework, it all starts with the right IT partner. A partner who truly understands your business and brings proactive expertise to keep you ahead of the latest threats.
Would you like help building the right-fit security roadmap for your business? Let’s chat.